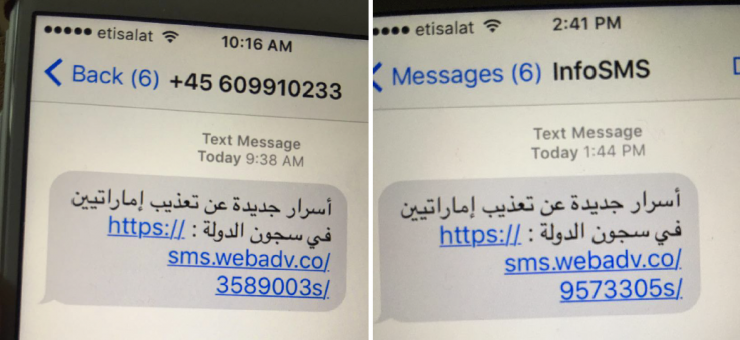
On the morning of August 10, Ahmed Mansoor, a 46-year-old human rights activist from the UAE, saw a strange text message from a strange phone number on his iPhone.
The content of this text message was very devious. It read "New information on prisoner abuse in the national jails in the UAE" and was accompanied by a link.
In the previous struggle, the UAE government used commercial spyware from companies such as FinFisher and Hacking Team to perform hacking operations on Ahmed Mansoor. As a result, Ahmed Mansoor became suspicious of the text message. Instead of clicking on the link, the text was forwarded to Bill Marczak, who worked for Citizen Lab at the University of Toronto's Munch School of Global Affairs.
The results showed that the message was indeed a problem, and the attached link pointed to a mature malware. This malware exploits three unknown vulnerabilities in the Apple iOS operating system, allowing hackers to fully control Ahmed Mansoor's iPhone. This is the conclusion of a joint report released by Citizens Laboratories and mobile security firm Lookout on Thursday.
This is the first time anyone has publicly disclosed such attacks. Prior to this, no one has ever seen using three unknown vulnerabilities (also known as zero-day vulnerabilities) to try to control the iPhone. The tools and techniques used for this attack are almost at the level of remote jailbreaking for the iPhone, worth as much as a million dollars. After these researchers warned Apple, Apple soon released an update on Thursday to fix these vulnerabilities.
The question is: Who planned the attack and what technologies did they use to implement it?
The researchers found that the spyware and zero-day exploits used in the attack were an unknown Israeli monitoring company NSO Group. According to Mike Murray, vice president of research at Lookout, the NSO Group is "essentially a cyberattacker."
Civic Lab and Lookout researchers were shocked by this unprecedented malware.
Mike Murray said: "No one has ever discovered this malware before. Basically, simply clicking on the link on the iPhone can jailbreak. It is the most mature network spyware we have ever seen in our industry ."
Since its inception in 2010, the NSO has gradually established its reputation as a government provider of sophisticated malware that monitors mobile phones. But before that, the use of NSO tools never appeared on any government documents. The NSO claims that its products are extremely covert, like "ghosts." The NSO itself is also like a "ghost", has no official website, and rarely accepts interviews or comment on reports. However, there are still some NSO information leaked out, including its acquisition of a US venture capital company’s $120 million investment in 2014 and a valuation of US$1 billion.
NSO’s malware, Pegasus, aims to quietly infect the iPhone and steal and eavesdrop all data and communications on infected iPhones.
Mike Murray explained: "Pegasus will steal all the information on the iPhone, eavesdrop on all calls, steal all text messages, emails, contacts. It will also add backdoors to all communication mechanisms on the iPhone. It can steal Gmail, Facebook, Skype. Everything in Apps, Whatsapp, Viber, WeChat, Telegram, etc."
With the help of Mike Murray and Lookout employees, Bill Marczak and John Scott-Railton of Civic Lab first clicked a link on a test iPhone to infect Pegasus to study the specific uses of Pegasus.
This attack against Ahmed Mansoor and another attack traced by citizen laboratories show that the famous Hacking Team and FinFisher are not examples, and other companies have joined the growing market that provides hacking services to the government. .
How is the NSO caught?
In May this year, Citizens Labs discovered a mature hacker group codenamed Stealth Falcon. Although unable to prove it, they doubted that Stealth Falcon is associated with the UAE government, mainly targeting dissidents in the UAE and abroad.
Through his research on Stealth Falcon, Civic Lab has figured out most of the infrastructure of the group, including servers and domain names used to steal data. However, civic labs cannot find malware samples used by these hackers. From the moment Ahmed Mansoor forwarded a message to Bill Marczak on August 10th, this changed.
After Bill Marczak and John Scott-Railton studied Pegasus, they traced the server and IP address that communicated with Pegasus, and the server and IP address were also included in the infrastructure that matched Stealth Falcon. Later, they discovered that the domain name registered by an NSO employee also points to the same IP address.
More importantly, Pegasus's developer left a string of information "Pegasus Protocol" in Pegasus, which clearly indicates the code name of this NSO spyware. The researchers also discovered more domain names associated with the NSO and its customer infrastructure, some of which were apparently designed to serve as phishing sites and were targeted at the staff of human rights organizations such as the Red Cross and news media organizations.
The discovery of Pegasus allowed researchers for the first time to truly understand the capabilities of the malware produced by the NSO. Since its inception in 2010, the NSO has become a legend in the industry, and the public knows nothing about it. NSO executives are rarely interviewed by the media, and reports about the NSO are also full of vague descriptions and unproven rumors.
NSO co-founder Omri Lavie told Defense News in 2013: “We are completely ghosts.â€
In a brief report in the Wall Street Journal in 2014, the Mexican government had already purchased NSO products, and even the CIA expressed its intention to purchase. The report also stated that NSO's spyware is sold worldwide.
Now that the NSO's spyware has been exposed and the zero-day exploits used have been patched, it should no longer claim to be a "ghost" anymore, although the NSO may have other zero-day loopholes and tools in hand. This is why researchers did not expect their reports and Apple's patch to stop the NSO for a long time.
Mike Murray said: "It is impossible for the NSO to go bankrupt simply by patching these holes."
What's more, Pegasus's settings can all go down to iOS 7, which means that NSO is likely to invade the iPhone on iPhone 5.
Zamir Dahbash, a spokesperson for the NSO, said in a statement: "The NSO's mission is to provide authorized governments with technology to help them fight terror and crime in order to make the world a better place."
“The NSO sells only to authorized government agencies and is fully compliant with strict export control laws and regulations. In addition, the NSO is not responsible for operating the systems sold. We are a strictly technical company. Customers who purchase our products must ensure that We use our tools legally. We are also listed specifically in our contracts and our products can only be used to prevent and investigate crimes."
Apple's reaction
Civic Lab and Lookout researchers contacted Apple immediately after discovering these zero-day vulnerabilities (Code Trident). Apple spent 10 days developing and distributing patches. This patch is now added to the iOS 9.3.5 update package. All iPhone users should download and install this update as soon as possible.
An Apple spokesperson said in a statement: “We immediately repaired these vulnerabilities and we added them to the iOS 9.3.5 update.†But the spokesperson declined to give further details.
Dan Guido, CEO of network security company Trail Of Bits, has extensive iOS security experience. He said that these attacks, which are rarely seen in the public eye, are not surprising. However, he said that despite the discovery of three zero-day loopholes, the iPhone is still much safer than Android phones.
Guido said: "Compared with other vendors, Apple has significantly increased the cost of invading Apple devices. However, this incident also shows the need for better intrusion detection methods for iOS. iOS remains the most secure consumer device on the market. The problem is that only if you have a skepticism and you have friends in a citizen lab can you know if you have malware on your iPhone.â€
Other victims
Researchers have yet to find samples of other Pegasus spyware. But by searching for similar links and domain names related to the attack and Stealth Falcon, they discovered a tweet that was suspected of targeting unknown Kenyan victims and another attack by Mexican investigative reporter Rafael Cabrera.

Rafael Cabrera was targeted by NSO malware for the first time last year and was attacked again in May this year. In the second attack, hackers tried to entice him to click on links in a series of messages, such as providing government corruption clues, warning messages consuming $500, and even a video link claiming to be his wife's derailment. Rafael Cabrera stated that he did not click any of the above links.
He said: "Obviously, they want me to click on the link, feeling a bit maddening."
Rafael Cabrera doesn't want to guess who is behind the scenes, the government or others. The Mexican government may be a client of the NSO, but it is not clear whether there is a police or intelligence department using the NSO's malware. Mexico is also the largest customer of the Hacking Team. Some Mexican government departments are accused of using these spywares to target journalists and dissidents instead of criminals.
In the end, neither Rafael Cabrera nor Ahmed Mansoor’s iPhone was hacked because they saw the hackers’ tricks. Of course, it can be said that they are lucky. Because there have been previous experiences of being hacked by the government, they are more alert than the average person.
But Bill Marczak of Citizen Labs said that what happened to them may signal future risks. If the government wants hacking tools and is willing to pay high prices, then the Hacking Team and NSO companies will continue to provide them. Civic labs have also documented several government hacking attacks against dissidents, journalists and human rights workers using spyware in the past. Tools are similar to those produced by NSO. Although civic laboratories exposed these attacks and issued warnings, there have been similar new attacks. Sometimes the attack is initiated by the same government, even for the same goal.
He said: “There is no incentive at all to allow these NSO companies not to sell hacking tools to such sophisticated criminals as the UAE.â€
This also heralds the rise of a new giant in the spyware industry. After the severe hacking of FinFisher and Hacking Team, the NSO has a lot of room to grow.
And if Ahmed Mansoor clicks that link on August 10, these things may never be discovered.
Via Vice
