At present, the architecture of existing digital home security systems at home and abroad is mainly based on traditional wired network technology. There are widespread problems such as cumbersome wiring, inability to achieve mobile access, long construction period, difficult maintenance, and poor scalability, which limits its Applications in digital home systems.
In view of the shortcomings of traditional home security systems, we use TCP/IP network technology and Bluetooth wireless communication technology to realize the true wireless home security system. The system can detect various situations in the home environment in real time, immediately notify the cell alarm center host in case of abnormal situation, and immediately display the specific location of the alarm location on the alarm center host screen, realize video linkage monitoring, and improve the alarm handling. Efficiency and accuracy. At the same time, the computer can also record the corresponding data for reference.
1, the composition of the home security system
The system consists of three parts: security intelligent control system, alarm center management system and remote login system. The overall system structure block diagram is shown in Figure 1.
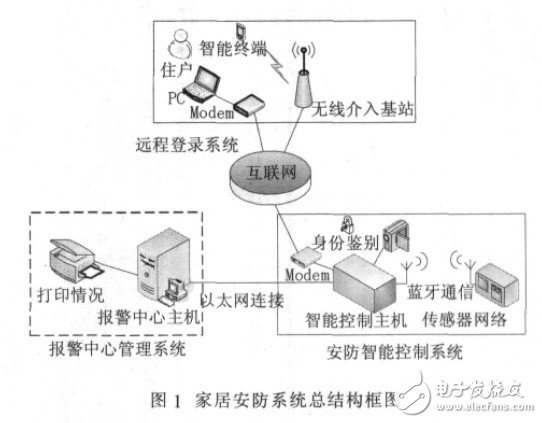
1.1 Security Intelligent Control System
The system uses the door magnetic and pyroelectric infrared probes, gas, temperature, smoke sensor, etc. as the main sensor, with Bluetooth wireless as the alarm form, with the intelligent control host as the alarm main body, and the safety of the whole room is placed in the wireless security alarm system. . Once the alarm occurs, the intelligent control host immediately connects to the cell alarm center host through the network to implement the on-site alarm, and uploads the alarm information to the alarm center. It is also equipped with a remote control alarm that can be controlled by the resident. In case of an emergency, the alarm can also be sent through the remote control. In addition, it also includes a household inquiry system, which enables residents to check the situation at home at any time through the terminal.
1.2 Alarm Center Management System
The system is placed in the community alarm center, equipped with duty guards, in order to deal with the alarms of the residents in the community at any time, greatly protecting the safety of the residents in the community. When a family has an alarm, the system obtains the police information through the network, and determines which alarm situation occurs in which room. The electronic positioning is implemented by the computer, and the video monitoring system is connected in parallel to timely understand the situation on the site so as to be timely and accurate. Processing. At the same time, the video of the room is extracted and saved.
1.3 Remote login system
The system utilizes an existing portable mobile terminal (smartphone or laptop) to log in to the security alarm system through a browser to query the home situation.
2, the realization of home security system
2.1 Security Intelligent Control Host System
The system mainly has alarm receiving and processing functions, Bluetooth communication signal processing functions, network functions supporting TCP/IP, and system setting functions. The system receives alarm information from common security sensors (displacement, infrared, gas, temperature, smoke sensor, etc.) through Bluetooth wireless communication. The login of the sensor and remote controller are also transmitted by the Bluetooth module, so a Bluetooth wireless transceiver is established in the system. The system uses TCP/IP technology for information exchange and control, realizes device status query, and realizes the interaction of alarm information and remote monitoring and control functions. The system is designed based on the above considerations.
In the system specificity, the system uses embedded system to achieve the ideal cost performance. The hardware system is mainly composed of CPU circuit, Bluetooth transceiver circuit, network interface circuit and power supply circuit. The circuit structure block diagram of the security system is shown in Figure 2.
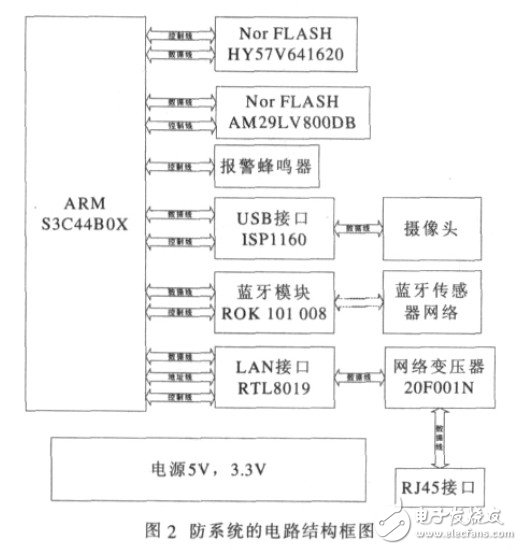
2.1.1 CPU circuit
The CPU is the core control component of the entire system, and almost all control of the system is done through it. The CPU of the system uses the ARM7TDMI-based chip S3C44BOX from Samsung to achieve a maximum frequency of 66MHZD, and the high-speed computing processing capability can handle most complex applications.
2.1.2 Network Interface Circuit
The RTL8019AS is a highly integrated Ethernet control chip with a communication rate of 10M. It is used to exchange data between the intelligent control panel and the alarm center management system.
2.1.3 Bluetooth transceiver circuit
The Bluetooth main module design uses Ericsson's Bluetooth module ROK101008. This module is a radio frequency Q baseband module suitable for short-range wireless communication. High integration, low power consumption, fully compatible with the Bluetooth protocol Version 1.1. Can be embedded in any device that requires Bluetooth.
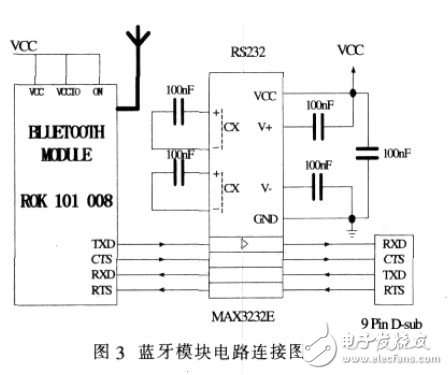
2.1.4 Image Acquisition Circuit
The system uses a low-cost USB camera as the image acquisition device, and is connected with the intelligent control host through the USB interface. This chip has an ARM7 core, which can be used to transplant the embedded operating system on this chip, or directly start the code to run the application.
2.1.5 Security Intelligent Control Host System Software Design
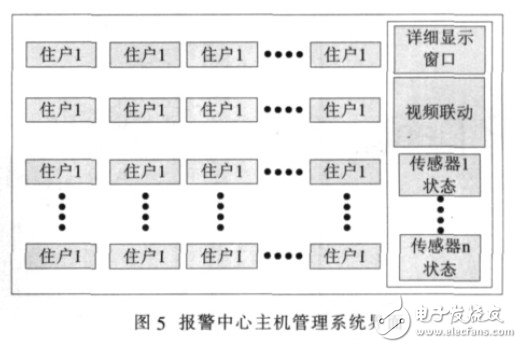
2.2 Alarm Center
The alarm center management system consists of a PC host and an alarm center management software.
2.3 Remote login system
Since the terminal access is very convenient now, it is not designed separately. Due to limited space, this part is not introduced too much.
3, the conclusion
The system fully considers the actual situation, and realizes automatic alarm through the network, real-time video monitoring, on-site prompts of the siren, online display of the location of the incident, user data and common telephone functions. It has good application value and considers the combination of video and alarm information. In order to ensure foolproof, there is centralized management of the host computer. Achieve flexible use of single or multiple users. Arbitrary conversion of centralized management and independent management, integrating alarm and monitoring. Make the application of the system more flexible and practical.
HDMI Adapter, Computer Adapters, Hd Adapter , Adapters for external ports, Electrical Adapters,Connect Adapter
Hdmi Adapter
Hdmi Adapter,Connect Adapter,Hd Adapter,Electrical Adapters
CHANGZHOU LESEN ELECTRONICS TECHNOLOGY CO.,LTD , https://www.china-lesencable.com
