One of the most tragic things in the world,
No more than your girlfriend is a hacker.
Because you never know,
What exactly does she have to monitor you.
Just today, a beauty hacker from China proved to the world that she had a way to monitor all communication data of a given mobile phone.

360 Unicorn Team Zhang Qiqiao
The beauty hacker named Zhang Qiqiao came from the 360 ​​Unicorn team. She shared this "sad" study at DEF CON, the world's top hacker conference. The hacker who announced this achievement with him is a single curiosity from the same team of 360 unicorns. (Single curiosity had installed a monitoring Trojan on her computer for her faithfulness to his girlfriend's watch. Perhaps this is why Zhang Qiqiao pulled him together to study this technology.)

Singer Curiosity (left) and Zhang Qiqiao gave speeches at DEF CON
Lies, cheating, 4G pseudo base stationsZhang Jianqiao told Lei Feng that in order to intercept the information on the mobile phone, all that needs to be done is to use a set of lies to trick the target phone. This set of lies comes from wolves in sheep's clothing: pseudo base stations.
You may have heard of this sinister base station, which is mainly used by Heinz to send and receive spam messages and phishing information. However, most of the pseudo-base stations you know use the following techniques:
1. Use high-intensity interference signals to block all 3G and 4G mobile phone signals in a region.
2. Most mobile phones will automatically search for 2G signals when they cannot connect 3G and 4G signals. At this point, the mobile phone is naturally led to the 2G signal of the pseudo base station, and then unknowingly receives the fraud information.
The reason why black production suppresses signals within 2G without directly attacking 3G and 4G signals is because these communication methods use a more stringent security model. However, this pattern of violently masked signals often results in the disruption of large-area cell phones that are communicating, and people will notice abnormal signals and try to leave the pseudo-base station area.
4G pseudo base station
And our beauty hackers chose to go directly to the 4G LTE signal. she says:
Since the 4G LTE signal adopts two-way authentication, it means that the base station needs to verify the identity of the mobile phone, and the mobile phone also needs to verify the identity of the base station. Once the mutual authentication is successful, both parties enter the encrypted communication mode, and it is very difficult to attack at this time. So my attack must be implemented before the completion of the authentication
The process of two-way authentication has become a good opportunity for Zhang Haoqiao to get rid of the mobile phone network. In the speech, she and Shan Qiu explained in detail the three steps of the attack:
1. Cheat the mobile phone number "ID card"
IMSI, a sound that is not sexy, is very important for mobile phones. It is the unique identifier of the mobile phone number on the operator's server. In other words, what you see is your mobile phone number, and in the operator's database, your mobile phone number corresponds to an IMSI number. This is like an "identity card" for mobile phones. All communication operations are based on the authentication of this ID card.
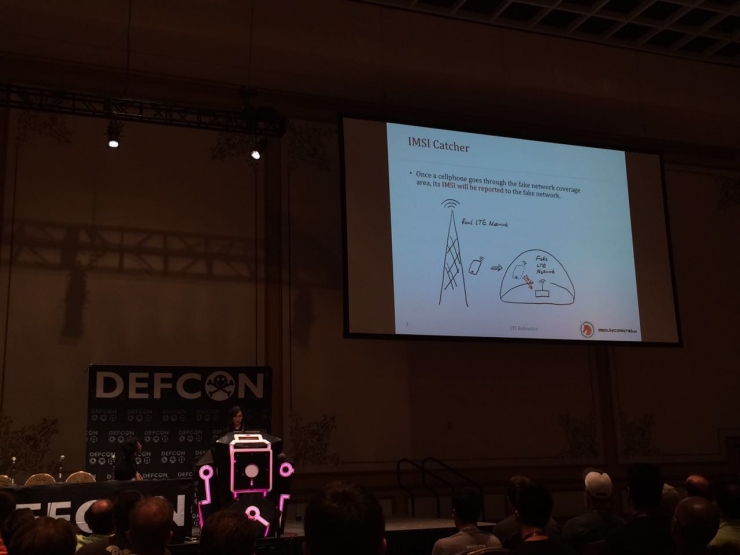
Mobile phone number "ID" IMSI capture method
For an attacker who sets up a pseudo-base station, an ID card that accesses the mobile phone can be used for the next attack. However, IMSI is like underwear for mobile phones: "Everyone has, but you can't just give it to people."
Zhang Qiqiao told Lei Feng Network (search "Lei Feng Network" public concern) :
In general, for the sake of security, when a mobile phone switches from one base station to another, a TMSI code is given to the other party. This code is temporary and has a short validity period. In general, a permanent IMSI code is only presented to the base station when the mobile phone searches for a signal for the first time—for example, when it is turned off and restarted.
This poses a thorny problem: When people are black, they can't usually rush to help others restart the phone.
In order to get the IMSI code collected by the attack, she needs to create a 4G pseudo base station. There is no way for the 4G pseudo base station to communicate directly with the mobile phone because its identity cannot be verified by the mobile phone. However, before the cell phone verifies the base station, the base station can first give the cell phone a video message:
After the mobile phone shows the "TMSI" code to the pseudo base station, the pseudo base station can send a message to the mobile phone, indicating that I still cannot judge your identity. According to the communication protocol, the mobile phone must present its IMSI code at this time.
In layman's terms, it is a fake security guard who stands at the gate and does not let visitors come in anyway unless he shows his identity card. In this way, the pseudo base station finally "cheats" to the "ID card" of the mobile phone number.
2, acting fake security
After getting a mobile phone number ID card, the "false security" (pseudo-base station) was not good enough to stop. He will tell the phone: The building is full, and you are no longer allowed to enter.
At this time, the mobile phone still did not have the opportunity to see the identity of the other party's "false security," and thus mistakenly thought that the Internet was full.
Because the signal strength of the pseudo base station is very large, it masks the real signal. So there is no other available network for mobile phones at this time. In order to save power, the phone will enter a state of closing the signal until you restart the phone next time.
At this time, aggressive mobile phones tend to be in a state of no signal for a long time until the owner notices and restarts manually. This resulted in a "denial of service attack" (DoS).
I believe you also thought that security without identity could do further bad things.

3, fall into the trap
Zhang Jianqiao told Lei Feng that there is a wonderful policy in the 4G LTE communication protocol:
When a base station considers itself to be overloaded, it can direct the incoming handset to the designated base station. So we can use a 4G pseudo base station to direct the handset to a 2G pseudo base station.
Back to the security example. This is equivalent to false security telling visitors that there is a small building next to the building where you can also handle your business.
That's right, that small building is basically a fake environment built by hackers - 2G pseudo base stations.
So, after such a big circle, the poor mobile phone finally fell to the grip of the 2G pseudo base station. Because in the 2G network, the mobile phone has no right to judge the authenticity of the base station, so the information will be handed over to the pseudo base station without reservation. The pseudo base station can even be used as a "middleman" to completely transfer the communication information to the true base station. From the user's point of view, there is no problem with his communications, but the reality is that all his communications are eavesdropped on by this "middleman".
3GPP's designated communication protocol over the years
Where did the wonderful rules come from?Maybe you will ask why the mobile phone must follow the base station's command to jump to the specified new base station?
Zhang Yuqiao said that this defect is not a loophole in a way. Because back in 2005, experts within the 3GPP of the 4G protocol development body had realized that this rule could theoretically lead to attacks. However, the agreement did not block this rule.
Because in the event of an emergency such as an earthquake or fire, it is likely that all mobile phones will connect to the same base station at the same time. This will cause the base station to overload and crash. The mobile phone is very "stupid" and often only searches for the nearest base station with the strongest signal. At this time, the mobile phone needs to obey orders and listen to the assignment of the base station to connect to another designated base station.
In the absence of changes to the communications protocol, all phones are in the midst of being attacked.
Good hackersFor Zhang Haoqiao, she was totally uninterested in monitoring the communication record of her boyfriend. To be exact, as a white hat hacker, she has strict bottom line and values.
Her research on cracking 4G LTE technology is to find a way to protect the mobile phone network and prevent such attacks from being exploited by the real bad guys.
At present, it is difficult to completely avoid such attacks without modifying the international 4G LTE protocol. The only improvement that can be made in this regard is the handset manufacturers. E.g:
1, because the attack will eventually go to the 2G pseudo base station, and 2G pseudo base stations have some of their own characteristics, if you add some identification conditions in the phone, you can identify most of the pseudo base stations, then you can remind the user Or simply refuse to connect.
2. For a denial of service attack on a 4G pseudo base station, the mobile phone can be automatically reconnected once every half an hour or even shorter in this state. This does not cause a long period of network disconnection.
Zhang Haoqiao told Lei Fengwang that many of the underlying logic structures have been studied in relation to the cracking of 4G LTE, in fact, thanks to the wireless communication expert Huang Lin of the Unicorn team. These two suggestions have been submitted by the team to their own cool mobile phones, and the corresponding resolution rules should be in preparation.
Although in real life, there is no evidence that such attacks have already occurred. However, Zhang Qiqiao and a single curious study tell people that the security of 4G networks is not a child's play. This kind of attack is difficult to detect and has a huge amount of lethality. When this kind of attack really begins to happen on a large scale, the price people will pay will be incalculable.
PS Zhang Jianqiao is particularly grateful to the teammates for their curiosity, Unicorn team communications, Niu Huanglin, and Unicorn team chief hacker Yang Qing. The research results were completed by the team.
Attached to the scene of Zhang Siqiao’s “siege†by otaku after the speech



New Folding Vanity Mirror,Special Folding Vanity Mirror,Fashionable And Cool Make-Up Mirror,Direct Sales Of Vanity Mirror
Dongguan City Diadia Industry Co.,Ltd , https://www.diadiabag.com
